A Hands-On Deep Dive Into CrowdStrike Identity Protection
By Eric Egolf, CEO
As system administrators navigating the intricate web of cybersecurity solutions, we often uncover hidden gems that revolutionize our approach to managing digital security. One such treasure within the CrowdStrike suite is the Identity Protection Module (IDP).
As we began exploring this module, we recognized the possibilities it offered but finding detailed guidance was a challenge. That’s why we created this “CrowdStrike Identity Protection Overview”- for other system administrators seeking insights. Our aim? To offer a guide, complete with step-by-step screenshots and real-life examples showcasing how this tool transformed our daily workflows.
Throughout this overview, we’ll weave through practical scenarios, complemented by illustrative screenshots, showing how seamlessly the IDP module integrates into everyday administrative duties. By recounting our experiences and tangible gains, our goal is to demystify this tool and reveal its true potential, equipping fellow administrators with a thorough grasp of its capabilities.
An Administrator’s Need for CrowdStrike IDP
As system admins ourselves, we understand the quest for tools that promise value and truly deliver it consistently amid the daily grind of managing systems. The IDP module is often overlooked but holds incredible power. The implementation of this module into our suite of services has transformed our workflows, mitigated risks, and augmented our ability to maintain a secure digital environment for ourselves and our clients in this ever-evolving security landscape. It has provided proactive detection capabilities beyond what even the EDR platform can provide. As we move further into access being controlled by user identities, this tool will only become more essential.
Exploring CrowdStrike IDP Features: A Closer Look
Let’s dive right into it.
You’ll find the Identity Protection tab beneath the Endpoint Security tab in the CrowdStrike Falcon portal.
Domain Security Tab AKA “Risks”
The next part of the portal is what I call “the risks” section. It is referred to as the Monitor section. The first link in this section is to your “Domain Security Overview”.
This area is where you’ll find highlights of all the currently flagged risks. As you expand each risk, you will see an option to “show related entities”. Clicking on this will provide a full list of all the objects with that particular risk.
Compromised Passwords
In the example below, we have a list of compromised passwords, or what I refer to as “solved passwords”. These indicate users that are using passwords that are in existing rainbow tables on the dark web. These passwords pose a risk since they are much more susceptible to brute-force attacks.
The domain security overview, or risk section, shows you things (presumably) under your control that you can configure (change password, change GPO settings, change machine settings, etc.) to reduce your attack surface.
Privileged Accounts
The next link is super cool and shows you all the risks for Privileged accounts. Obviously, these represent a greater risk than other accounts because they have some level of administrative privileges in your environment.
One of the awesome capabilities this tool allows you is the ability to identify privileged accounts with “stealthy privileges”. That includes stale accounts, ones with compromised passwords, etc.
One cool thing I wasn’t aware of until we dove deeper was the honeytoken concept. This involves creating a deceptive account designed to lure potential attackers, labeling it as a “honeytoken account”. If it is ever accessed, it triggers an alert, so you know that you have a potential compromise on your hands.
CrowdStrike IDP provides this same view for all users, with ways to customize the widgets. It makes it easy to look at top user account lockouts, password changes, top password failures, and more; all with the same cool widget summarization seen above. It also offers links for risk analysis and event analysis (we don’t use these much ourselves, but they are powerful when needed).
Identity-Based Incidents Tab AKA “Detections”
Moving on from the risk section, we delve into the concept of detections. In CrowdStrike IDP this is called the Identity-Based Incidents tab. In the screenshot below you can see 3 detections (with names redacted).

Clicking on each gives you the expanded details (see below).
This gives us a summary of the accounts involved in the identity-based incident. In this case, it lets me know that a single account was involved and the alert was triggered because it logged into multiple servers.
Threat Hunter
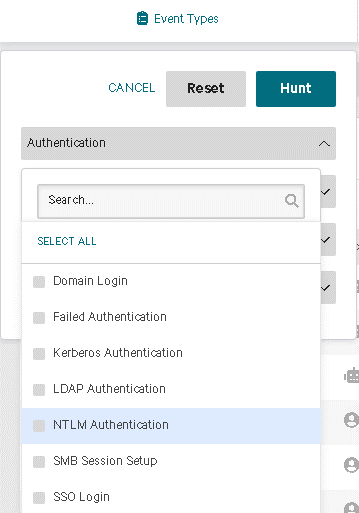
From there, I can move to the Threat Hunter section, prefiltered with this user (see below). In this example, we can see all the systems this user accessed and with which protocols. This gives us a more complete picture and helps us determine if further investigation is necessary.
The Threat Hunter is, in my experience, the best tool for quickly looking through authentication logs. This allows you to quickly filter based on event types, identities, source, and destination endpoints. A highlight here is that the event types are nicely enumerated for you. This means you don’t have to spend time trying to translate Windows event IDs. Everything is spelled out neatly in the search itself making it far more convenient than sifting through Windows event logs or creating custom parsers.
This tool simplifies understanding authentication and timelines, offering straightforward and intuitive filters that streamline the process significantly.
“Enforce” Module
CrowdStrike IDP features an enforce module, and although we’re still exploring its capabilities, the most impactful use case we’ve witnessed involves implementing MFA enforcement for all privileged accounts using the RDP protocol. Anyone in the system admin space knows how hard this normally is.
With CrowdStrike IDP, it’s as straightforward as crafting a policy and ensuring the machines have the standard Falcon agent installed. Just like that, you can enable RDP MFA (using options like Microsoft Authenticator or any number of the other authenticators provided by CrowdStrike IDP) for all privileged accounts.
Programmatic Accounts
Additionally, you can also block RDP access for all “programmatic accounts” a concept tracked within CS IDP.
Hackers often exploit credentials from service accounts (known as “Programmatic Accounts” in CS IDP) which makes it amazingly powerful to have policies that prevent these accounts from using RDP with a simple, singular policy enforcement definition.
Regarding programmatic or service accounts, another noteworthy feature is the account profiling tool. For example, a service account usually runs on a single machine or has a very specific use pattern. Once that is profiled (after 60 days), if CrowdStrike detects a login to a system outside of this established profile, it triggers an alert. This gives you a new layer of detection capabilities that EDR and other systems would miss.
The ability of CS IDP to profile the login patterns of every account (including stale accounts) and alert you to anomalies in their usage relative to the normal pattern is extremely powerful. This.
Connectors
Finally, we have the connectors. In the example below, there’s a connector to Azure AD which is another identity provider outside of AD. CrowdStrike IDP pulls in this other Identity Provider data, giving you detections on this dataset just like the normal Active Directory detections discussed above. Setting this up is straightforward—simply create an enterprise app in Azure AD and connect it.
Currently, at the time of this writing, it can use Azure AD and Okta as external identity providers for monitoring and detection purposes.
In Conclusion: CrowdStrike IDP is Powerful
The key takeaway here is that CrowdStrike IDP stands as an extremely powerful tool. Hopefully, this brief dive into some of the uses and settings gives you the confidence to try enabling it and exploring the functionality in your CrowdStrike Portal. We believe it’s one of the best security investments you can make!





